Data Flow Diagram Cyber Security Security Conceptdraw Firewa
Security network diagram model cloud diagrams government computer solution devices conceptdraw example access networks architecture solutions cybersecurity information models examples Network security model Cyber security threats and data flow diagrams
Network Security | Firewall between LAN and WAN | Network Security
Network security model Cyber security isometric flowchart royalty free vector image Risk assessment flowchart for cyber security management
Security event logging, why it is so important – aykira internet solutions
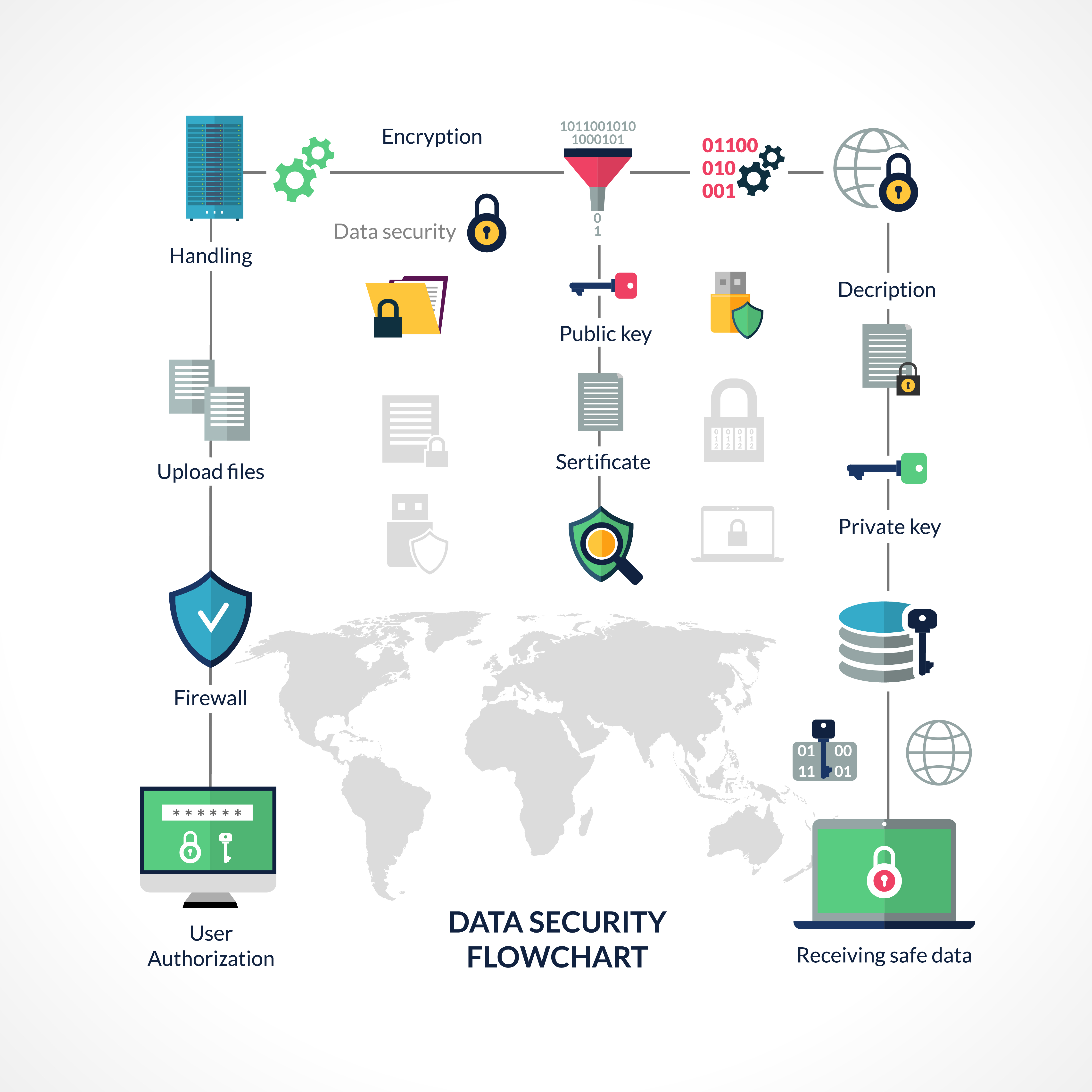
Cyber security: a paradigm shift in it auditingData flow diagram of smart security framework Cyber security flowchart royalty free vector imageCyber security flow chart.
Iot & enterprise cybersecurityNetwork security tips Cyber security diagramSecurity conceptdraw firewall firewalls architectures infrastructure networking systems lan devices create wan protecting realtek privacy.

Flow chart of cyber investigation : cyber crime awareness society
Incident cyber response template plan structure immediately planning usable guidanceFlow chart on cyber security from research paper Security network diagram control computer diagrams devices networks secure access encryption solution cloud examples model architecture example conceptdraw software systemData flow and security overview.
Rfid vmCyber security compromise flow chart Cyber security flow chartCybersecurity and digital business risk management flow diagram of.
Data flow diagram
Flow chart cyber security compromise australiaRfid vm security system flow chart Cyber security flow chartData flow diagram in software engineering.
Security flow cyber data event logging diagram logs internet important why so together putting events auNist cybersecurity framework Cybersecurity incident response plan template and example ukFlow cybersecurity chart.

Process flow vs. data flow diagrams for threat modeling (2023)
Crime evidence ipcCyber security incident response process flowchart ppt powerpoint Cybersecurity procedures implementation yokogawa customer developing implement solutions benefits accordance practicesSecurity cyber network tips cybersecurity computer steps infographic diagram degrees diagrams conceptdraw example networks solutions architecture solution information risks threats.
Cyber incident flow chartCyber security incident response process flow chart deploying computer Cybersecurity policies & proceduresArchitecture cybersecurity enterprise iot cyber security diagram system software.

Cyber security flowchart
Cyber security framework mind map templateFree vector Network security.
.







